At e-Builder, A Trimble Company (“e-Builder”), our goal is to deliver highly available, scalable, and secure products and services that you can rely on to efficiently manage your capital program.
Availability
Availability of e-Builder Enterprise services
We continually monitor the performance of our services to prevent possible incidents. We consolidate views from log parsing, infrastructure monitoring, and application performance management (APM).
The e-Builder Trust Site provides information on our availability and performance (response time).
Disaster recovery
e-Builder ensures all its services have disaster recovery plans in place covering disaster prevention and recovery. e-Builder aims to provide a robust recovery plan should any disaster occur while taking all possible steps to prevent such a situation.
Our prevention and recovery plans:
- Reduce the likelihood of a disaster
- Implement contingency plans to restore partial or full service as soon as possible after an incident has occurred
- Document a clear communication strategy to keep all those involved (especially customers) informed of the situation as it develops.
Infrastructure
Amazon Web Services
e-Builder hosts its assets and data in Amazon Web Service’s (AWS)
Amazon Web Services (AWS), the world’s leader in cloud infrastructure, is designed to deliver a flexible, reliable, scalable, and secure cloud computing environment with high-quality global network performance.
AWS provides secured data centers all around the world.
AWS data centers are protected from unauthorized physical access and environmental hazards by a range of security controls.
The AWS platform offers exceptionally high-security compliance, including certifications like ISO27001, SOC 2, and FedRAMP.
Cloud security
Cloud and data security are shared responsibilities between the cloud infrastructure provider and the client utilizing the cloud solution.
In our case, it means that we trust Amazon Web Services to manage the security of the cloud infrastructure, and we are responsible for the security in the cloud environment.
Hosts are hardened with automatic (Linux) & scheduled(Windows) patching, isolated VPC, data encryption, robust vulnerability management practices which include penetration testing, role-based access control, and security groups.
We utilize managed services like AWS Shield.
We have an in-house 24x7 SOC team for monitoring alerts using top tier endpoint detection and response solutions and other security engineering tooling.
You can read more about cloud security in AWS Whitepapers & Guides.
Data
Access control
e-Builders application segregates its customers’ data logically internal to the system. Each company is assigned a GUID (Globally Unique Identifier) that isolates them from other accounts. The customer’s end-users are then attached to the correct account by the customer’s admin. The customer’s admin can only create users in their specific account with their GUID assignment. This structure drives the segmentation of the data and the security controls across the application.
The e-Builder Enterprise product is architected with a role-based security model. This security model allows administrators at various levels to control access to data. e-Builder Enterprise manages roles with the configuration of account and project level groups and handles exceptions at the user-level. Users are placed into a group(s) and inherit the access permissions granted to that group(s).
e-Builder restricts access to its premises and customer data and protects its source code repositories by using, among other measures, multi-factor authentication to access production systems.
Encryption of Data
All customer data is encrypted at rest.
Encryption in transit is enforced for the data in transit, giving industry-standard levels of security available for data transmission over the Internet.
We rely on AWS technology to achieve Server-side encryption for our document store and other storage volumes encryption.
Transport Layer Security protects all our HTTPS end-points.
Our web services are forcing secure transport thanks to HTTP Strict Transport Security (HSTS).
Data in transit and at rest encryption uses the AES256 standard.
Single Sign-On
Single Sign-On (SSO) is an optional integration feature that allows users to integrate e-Builder applications with their SSO provider.
e-Builder Single Sign-On requires a standard SAML 2.0 connection setup on both parties.
It allows users to authenticate to e-Builder without having to enter credentials within e-Builder.
e-Builder supports all the providers as long as they can set up a standard SAML 2.0 connection.
Multi-Factor Authentication
Multi-Factor Authentication is a security feature that is available to all the customers, which require users to validate their authentication using two or more items of evidence.
All the administration tools required MFA. This feature is available as optional authentication for all customers.
MFA works by entering a username, password, and code provided by an authenticator service like Google Authenticator (Something you are, Something you know, Something you have).
Data Backups
We actively maintain data backups so that in the event of data corruption, inconsistency, or loss, we can restore data as quickly as possible.
Backups are maintained separately to the primary data repository but within the same geographical region.
We maintain internal targets for Recovery Time Objective (RTO) (the maximum time expected to restore the system to operation) and Recovery Point Objective (RPO) (the maximum expected loss of data in the event of a disaster).
Data Retention
Data is retained until 90 days after contract termination unless otherwise requested/specified by the customer. At the end of that period, the customer data gets purged from the database and project documents removed from the file store. The database information will still be part of previous database backups until the standard backup retention period (90 days after deletion).
Data Deletion
After contract termination, if requested by the customer via optional services, we provide a copy of customer data in the form of a Microsoft SQL Server Database (database extract) and the archive of project documents stored as part of the customer account.
Compliance
Compliance and best practices
At e-Builder, we include security throughout the whole development lifecycle. We utilize industry standards wherever possible to ensure consistency and best practices across the organization and in all the products and services we deliver.
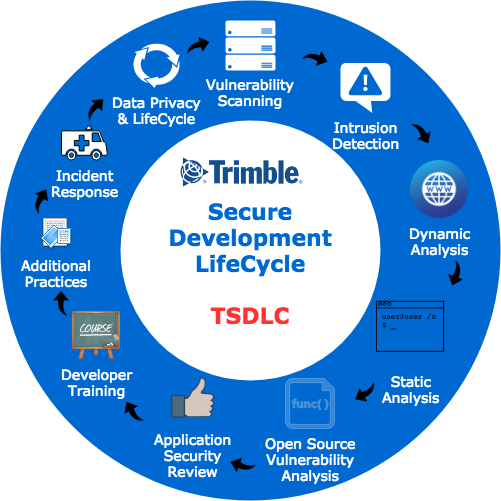
Trimble Secure Development Life Cycle
Within the Trimble Secure Development Life Cycle (TSDLC) framework, we ensure that security is embedded and operationalized so that our deliverables will meet consistent security levels. Equally important, we monitor and manage infrastructure and environments. These tools include identity and access management, vulnerability management, and intrusion detection solutions on our networks and systems. These tools, complemented with appropriate incident response, work together to ensure security for our customer solutions. Within the Trimble Secure Development Life Cycle framework, we review our cloud infrastructure and processes according to industry best practices. We are continuously executing 24x7 security monitoring, vulnerability scanning, intrusion detection, dynamic and static analysis, and open-source analysis of our solutions. We perform application security assessments both ourselves and by utilizing 3rd party security experts.
Vulnerability Scanning
We use vulnerability scanning tools to proactively expose security vulnerabilities in our cloud-based systems.
Third-Party Component Analysis
Like most software providers, many of our software products include underlying components from third-party suppliers that are necessary building blocks for our software. We use third-party component analysis tools to scan these components to check if there are newer versions or patches available, check for any known vulnerabilities, and confirm licensing compliance.
Intrusion Detection
In a world of increasingly sophisticated cyberattacks, e-Builder employs intrusion detection tools to detect attacks on our cloud service endpoints (points of access) and our internal systems.
Static Source Code Analysis
Static code analysis is the analysis of computer code directly, i.e., without actually executing programs. Analysis of source code is a useful method of detecting security threats in the system before it is deployed and released.
Dynamic Code Analysis
Dynamic analysis is typically used in association with static code analysis and looks at a “live” or “staged” system as opposed to the code directly.
Anti-Virus
Many of our applications provide features that allow customers to upload files and data in various forms. We employ anti-virus scanning tools to check data as it is uploaded to remove or quarantine data.
Cybersecurity Awareness
A prerequisite for developing secure solutions is understanding the threat landscape in which the service is operating. In Trimble, threat modeling is one of the core guiding principles when designing and developing our solutions.
Within Trimble, we regularly update our knowledge about cybersecurity topics and share awareness about cybersecurity threats among all parties responsible for managing and developing our solutions. As a baseline, all employees attend mandatory cybersecurity training sessions. Solution architects and developers participate in specialized cybersecurity training sessions addressing threats specific to the product developed by e-Builder.
External Certifications
SOC 1 Type II
e-Builder SOC 1 type 2 has been certified in accordance with the AICPA SSAE NO.18 and IAASB ISAE 3402 Standards.
SOC 2 Type II
e-Builder SOC 2 type 2 was certified in accordance with the AICPA SSAE NO. 18 and IAASB ISAE 3000 Standards.
SOC 3 ISAE
e-Builder SOC 3 ISAE was certified in accordance with the AICPA Attestation and IAASB ISAE No. 3000 Standards. See report.
Trimble ISO 27001
e-Builder relies on specific services on Trimble Cloud xOps for Operational Support, Security Operations, and Developer Virtual Private Network (VPN) Service. Trimble Cloud xOps is certified by ISO/IEC 27001:2013 and has an independent 3rd party conduct yearly surveillance audits with every 3rd year being a full audit of our Information Security Management System (ISMS).
Additional Product Offerings
Government Edition
e-Builder offers clients a more secure production environment option for e-Builder Enterprise, e-Builder Enterprise Government Edition. The e-Builder Enterprise Government Edition production environment provides the following:
- FedRAMP Moderate Impact Level Security (which requires 325 controls)
- Governance-focused, audit-friendly services features
- Hosted on AWS GovCloud Region (which is FedRAMP authorized and ITAR compliant)
- To learn more about the AWS GovCloud (US) Region: Click Here.
- A security program is established and managed but Trimble Cyber Security and vetted by a FedRAMP Third Party Assessment Organization.




